Jun 5, 2025
Role-Based Access Control (RBAC) simplifies API security by assigning permissions to roles instead of individual users. This approach ensures users only access what they need, reducing risks and improving efficiency. Here's why RBAC is critical:
RBAC is essential for securing APIs, especially in environments with frequent access changes or sensitive data. Keep reading to learn how to implement and maintain an effective RBAC system for your APIs.
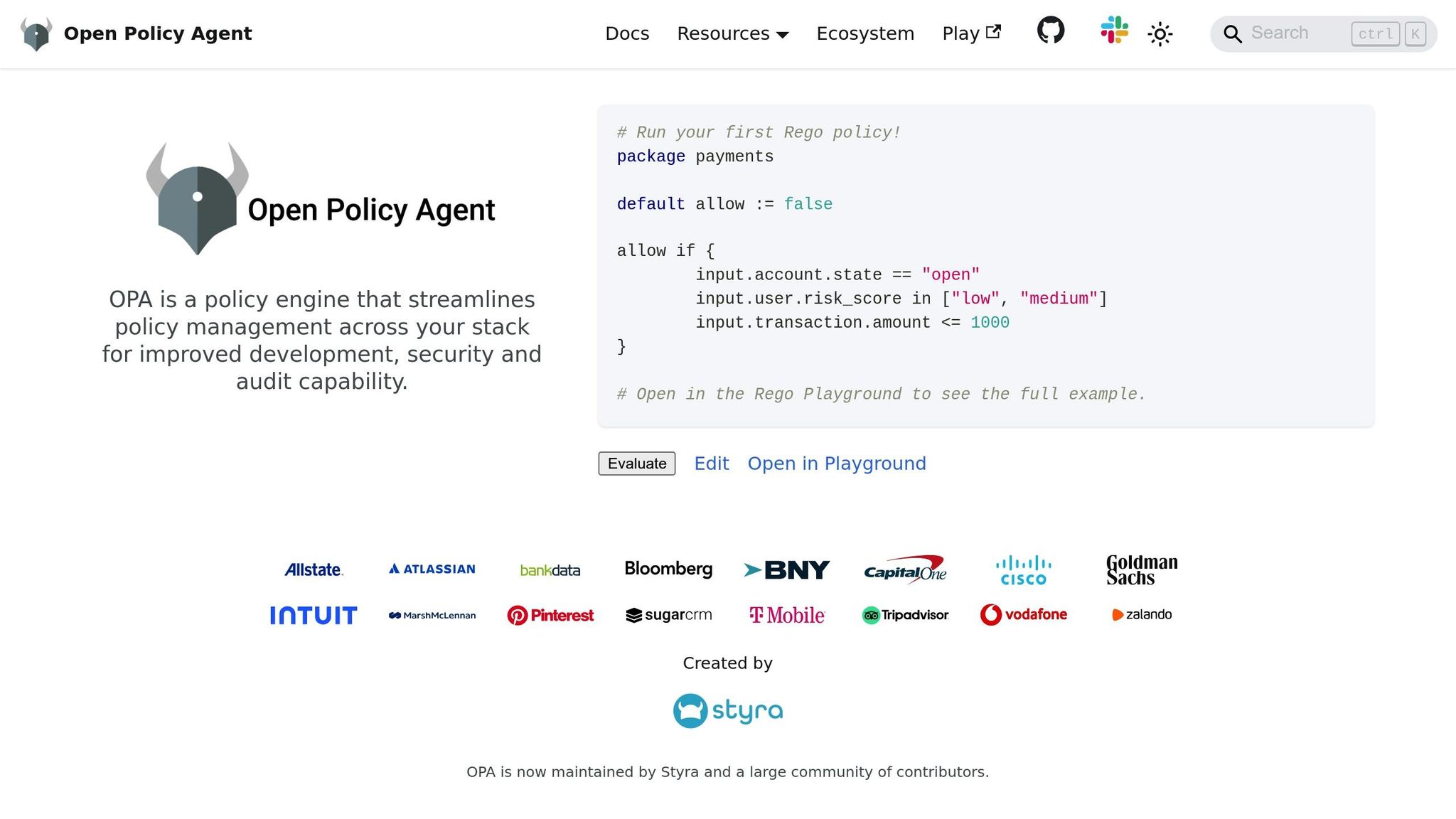
Creating an effective Role-Based Access Control (RBAC) system for APIs requires careful planning to balance security, scalability, and efficiency. These principles lay the groundwork for a reliable access control system, ensuring your API can handle real-world demands securely.
Role hierarchies simplify permission management by reflecting the structure of your organization. Higher-level roles automatically inherit permissions from lower-level ones, making it easier to assign and manage access. This can be done through an inheritance hierarchy, where senior roles gain all subordinate permissions, or an activation hierarchy, which allows users to switch roles during a session for added security.
Separation of duties (SOD) helps prevent conflicts of interest by ensuring users don’t hold roles that could lead to misuse of privileges. Static SOD enforces this by preventing a single user from being assigned conflicting roles - for example, someone authorized to write checks cannot also approve them. Dynamic SOD, on the other hand, permits users to hold conflicting roles but ensures they cannot activate both roles in the same session. This often involves requiring two separate users to authorize sensitive actions. Together, these measures support the enforcement of minimal permissions.
The principle of least privilege is a cornerstone of API security. According to NIST, it’s about assigning users only the permissions they need to perform their job - nothing more. This minimizes security risks and supports compliance with regulations like GDPR, PCI DSS, and HIPAA.
To implement this principle effectively, start by understanding the specific permission needs of your API. Tools like Graph Explorer can help identify the minimum permissions required for each API call. Remove unused permissions and replace broad permissions with more restrictive ones wherever possible. This meticulous approach ensures that users and applications only have access to what’s absolutely necessary.
Once roles are clearly defined, the next step is to align API resources with these roles. This involves grouping related API endpoints under specific roles. For instance, endpoints dealing with patient records might fall under a "healthcare data" role, while billing-related endpoints could be grouped under "financial data".
To improve performance, use a caching layer to store role-to-permission mappings and refresh it when organizational changes occur. Additionally, dynamic management tools, such as admin interfaces, allow for role updates without requiring system downtime or code changes. Regularly test these mappings to ensure permissions are correctly enforced, both for allowed and denied scenarios. Keeping an audit trail of changes to roles and permissions is essential for compliance and security reviews.
Finding the right balance between granularity and simplicity is crucial. Roles should reflect actual job functions while remaining flexible enough to handle exceptions, such as temporary permission adjustments or role combinations for unique cases.
Turning RBAC (Role-Based Access Control) design principles into a functional system for APIs requires thoughtful planning and precise execution. This section focuses on how to implement RBAC effectively in a live API environment, ensuring your API resources are secure while maintaining usability and performance.
Start by defining roles based on specific job functions. Conduct an audit of current access patterns to identify the resources your RBAC system will cover and how users interact with them. This initial analysis helps you spot potential security gaps and understand existing access behaviors.
Create a hierarchical structure for roles, starting with broad categories and refining them based on actual usage. For example, roles like Admin (full access), Developer (project-related access), and Member (limited access) can form the foundation of your hierarchy. This structure ensures access aligns with the principle of least privilege.
For each role, document the specific API endpoints, HTTP methods, and data types they can access. Test these permissions thoroughly to confirm they work as expected and ensure the user interface remains intuitive. Testing is critical to uncover potential gaps or overly restrictive permissions that might need adjustment.
Once roles are set, assign every user to at least one role. Unassigned users create security risks and complicate access management. Establish clear processes for role assignments, including approval workflows for sensitive roles and regular reviews to keep access permissions up to date.
Dynamic role assignment is a game-changer for flexibility, allowing you to modify user permissions without requiring them to log out. Token-based authentication is central to this approach. Design tokens to include role information that can be refreshed or updated as needed. Middleware can then validate and refresh tokens or session data before performing role checks.
To simplify updates, use a "policy as code" approach to separate access rules from application logic. This makes your system easier to maintain and allows you to update policies without deploying new application code.
Automate initial role assignments by integrating with identity providers. Use attributes like department, job title, or location to assign roles automatically . With dynamic tokens in place, you can make immediate permission changes as needed, ensuring your system stays responsive to organizational needs.
Real-time permission updates ensure that access changes take effect immediately, even during active user sessions. This capability is crucial for organizations with frequent role changes or urgent access requirements.
To enable real-time updates, leverage a centralized framework that includes a Policy Decision Point (PDP), Policy Information Point (PIP), Policy Administration Point (PAP), and Policy Enforcement Point (PEP). These components work together to evaluate and enforce permissions instantly. Dynamic authorization ensures each request is checked against the latest policies and user attributes, keeping access controls up to date.
By externalizing authorization logic from your application’s business logic, you can centralize and audit access rules more effectively. A Policy Decision Point evaluates policies independently, making it easier to update rules without affecting core application functionality. This separation minimizes deployment risks and speeds up policy adjustments.
However, real-time updates can impact API performance. Frequent policy checks might slow down response times, so consider caching frequently accessed permissions. Ensure the cache is promptly invalidated when permissions change. Alternatively, use event-driven architectures to push updates to relevant services, reducing the need for constant polling.
Even with real-time capabilities, regular auditing is essential. Schedule automated reviews to ensure your RBAC implementation remains effective and to catch issues before they disrupt users or compromise security.
When your system's API demands increase, it's critical to ensure that your Role-Based Access Control (RBAC) framework scales effectively. A scalable RBAC setup not only safeguards security but also ensures consistent performance as usage grows.
Role inheritance simplifies managing permissions in complex systems. Instead of creating numerous roles with overlapping permissions, you can establish a hierarchy where child roles automatically inherit permissions from parent roles. For instance, a "Senior Developer" role could inherit all permissions from the "Developer" role, while adding rights for tasks like code reviews and deployments. This approach reduces administrative overhead and keeps configurations manageable.
However, excessive role inheritance can backfire. If not carefully managed, it might grant users more access than necessary. To maintain control, document your role hierarchy and role-creation policies thoroughly. A well-structured RBAC model should make it easy to add users, roles, and permissions without complicating the system.
Once your role hierarchy is in place, focus on optimizing performance with caching strategies.
Caching is a game-changer for RBAC performance. By storing frequently accessed permission data, caching can reduce database queries by up to 90% and server load by 50%, significantly improving system responsiveness.
For best results, implement multi-level caching for user-role mappings, role-permission relationships, and complex permission evaluations. Using in-memory stores allows retrieval in microseconds, making permission checks nearly instantaneous.
Set Time-To-Live (TTL) values that match how often your permissions change. For example:
Security is a top concern when caching RBAC data. Protect cached data by:
Organizations that follow these practices have reported a 50% drop in unauthorized access incidents.
Next, consider how architectural choices - stateless versus stateful designs - affect scalability and performance.
Your choice between stateless and stateful RBAC architectures can shape your system's scalability and functionality.
| Aspect | Stateless RBAC | Stateful RBAC |
|---|---|---|
| Scalability | High – any server can handle requests | Limited – session dependencies |
| Resource Usage | Lower – minimal impact from server loss | Higher – server loss affects sessions |
| Permission Revocation | More complex – may require token invalidation | Simpler – update server-side data |
| Development Complexity | Simpler – no state management needed | More complex – requires session handling |
For many API-focused applications, a hybrid approach works best. Use stateless JWT tokens for routine API calls, and integrate stateful elements for critical functions like permission revocation. When implementing stateless RBAC, ensure JWT tokens:
For added security, consider using multiple API keys with varying access levels instead of relying on a single token.
Ultimately, your RBAC model should align with your API's specific needs. Stateless designs are well-suited for high-traffic APIs with stable permissions, while stateful elements are better for systems requiring frequent updates or detailed audit trails.
To keep Role-Based Access Control (RBAC) systems effective, they need ongoing care and updates. Without consistent maintenance, even the most well-planned systems can become weak points over time, exposing your organization to security risks.
A solid RBAC system relies on constant monitoring. Every access attempt, role change, and permission update should be tracked to ensure complete visibility into who is accessing what and when. Audit logs are critical - they should detail who made changes, when they occurred, and what was modified. These logs are essential during security investigations or compliance checks.
Regular access reviews are another must. Over time, inactive users and outdated permissions can pile up, creating unnecessary vulnerabilities. Periodic audits are key to identifying and removing these obsolete permissions.
Automated tools can make monitoring easier by generating reports on user roles, permission usage, and any unusual activity. Setting up alerts for suspicious behavior - like multiple failed login attempts or access requests during odd hours - adds another layer of security.
For organizations bound by regulations like HIPAA, SOX, SOC 2, or ISO 27001, RBAC simplifies compliance by providing an auditable trail of access activity. Employee training is just as important. Staff should understand security protocols, follow access procedures, and be aware of the risks tied to non-compliance.
These measures not only strengthen security but also prepare your system to adapt as your organization evolves.
As your organization grows and changes, your RBAC system must evolve too. Roles should be updated regularly to reflect new teams, shifting responsibilities, and expanded functionalities. To prevent "role creep", where users accumulate unnecessary permissions, consider automating access updates through integration with HR systems and conducting frequent role reviews.
Policy-based access control can help manage complexity by defining broader security policies that work across various scenarios while maintaining clear boundaries. Establishing a governance structure with dedicated decision-makers ensures roles stay aligned with job functions and security needs. Keeping well-organized documentation of roles and responsibilities also makes it easier to manage changes.
Monitoring access logs can reveal patterns that signal when adjustments to the RBAC framework are needed. This proactive approach ensures that your system remains relevant and secure.
To prepare your RBAC system for the future, focus on scalability and adaptability. As APIs and technologies evolve, your system should be able to adjust without requiring major overhauls.
One way to enhance security is by implementing context-aware authorization. This method considers factors like device reputation, location, network conditions, and user behavior when making access decisions. It provides a more nuanced approach without creating an overwhelming number of roles.
Layered enforcement is another effective strategy. Instead of relying solely on gateway-level permissions, include checks at multiple points within your architecture. Combining RBAC with Attribute-Based Access Control (ABAC) or Policy-Based Access Control (PBAC) can provide the flexibility needed for dynamic access decisions while avoiding role overload.
Using tools like Policy as Code frameworks (e.g., OPAL) allows you to manage RBAC configurations like application code. This makes it easier to track changes, roll back issues, and ensure consistency across environments. Integrating these frameworks into CI/CD pipelines can catch authorization errors before they reach production.
Looking ahead, technologies like machine learning and AI are expected to enhance RBAC systems with intelligent role recommendations, anomaly detection, and automated policy updates. Zero-trust architectures are also incorporating role-based controls to continuously validate access rights based on real-time risk assessments. Additionally, as API ecosystems shift toward more user-centric models, decentralized identity management and user-controlled consent mechanisms will become increasingly important.
The goal is to create RBAC systems that adapt proactively to change. By focusing on thorough monitoring, staying aligned with organizational needs, and preparing for emerging technologies, your RBAC system can remain a strong foundation for security and support your organization’s growth.
With a solid implementation and consistent monitoring, the following highlights the key principles for designing effective RBAC systems for APIs.
RBAC makes API security more manageable by transforming complex permissions into straightforward roles.
"Role-Based Access Control (RBAC) simplifies API permission management by assigning users to predefined roles, each with specific permissions".
At its core, the principle of least privilege is essential for successful RBAC design. By ensuring users have only the permissions required for their roles, organizations can significantly minimize their attack surface. It's worth noting that valid account abuse remains one of the most common cyberattack methods.
Leveraging least privilege and scalable role hierarchies not only reduces risks but also simplifies compliance efforts. A role-based structure can easily adapt to organizational changes, while built-in audit trails assist in meeting regulatory obligations. Regular access reviews and role hierarchies also help maintain a balance between strong security and API performance.
Emerging technologies like AI and machine learning are beginning to refine RBAC systems further.
"Organizations seeking to integrate AI into their RBAC systems should start with a detailed evaluation of their current roles and identity data... Without clean and well-defined roles, AI might amplify existing inefficiencies rather than solve them".
RBAC implementation goes beyond technical execution - it's about creating a security framework that aligns with and supports your business goals. With API security incidents impacting a majority of organizations, robust access control has become a necessity.
"Effective RBAC is not just about assigning roles - it's about ensuring that the right users have the right level of access at the right time and that the system is continuously maintained and updated to reflect the business's evolving needs".
To succeed, roles should be defined based on actual job functions and updated regularly to account for organizational changes. Consistently applying the principle of least privilege and establishing review processes from the start are crucial. RBAC demands ongoing attention and adaptability, but the effort leads to reduced security risks, easier compliance, and smoother operations over time.
To put the principle of least privilege (PoLP) into action within Role-Based Access Control (RBAC) for APIs, the goal is simple: ensure users have only the permissions they need - nothing more, nothing less. Start by creating roles tailored to specific job functions, keeping access rights as limited as possible. Avoid assigning overly broad or generic permissions that could lead to unnecessary exposure. As job responsibilities or organizational requirements shift, make it a priority to revisit and adjust these roles accordingly.
Another key step is automating the assignment and removal of roles. This minimizes the chances of human error and ensures that permissions are granted strictly on an as-needed basis. Regularly auditing access logs and permissions is equally important. These reviews help uncover any inconsistencies or outdated permissions, allowing you to correct them promptly. By sticking to these practices, organizations can reduce potential security risks while keeping API access both efficient and secure.
Using role hierarchies in Role-Based Access Control (RBAC) brings several advantages when it comes to API security and management. This system allows higher-level roles to automatically inherit permissions from lower-level roles, which simplifies how access is controlled. Instead of managing an overwhelming number of individual roles, you can streamline permissions, making administration far more manageable - especially in systems with layered access requirements.
Another benefit is the added security. Role hierarchies ensure that users only access the resources they need to perform their specific tasks, reducing the chances of unauthorized access. This not only helps enforce security policies but also provides clearer visibility into who has access to what. As a result, auditing permissions and maintaining a secure API environment becomes much easier.
Dynamic role assignment brings a new level of flexibility to Role-Based Access Control (RBAC) systems in API environments. By allowing user roles to adjust in real time based on factors like behavior, location, or specific requests, it ensures access permissions can adapt instantly to shifting needs. This eliminates the limitations of rigid, static role definitions.
Take a financial application, for example. A user's ability to approve transactions could change dynamically depending on the transaction amount or its context. This not only enhances security by limiting access to sensitive actions but also boosts efficiency in handling complex scenarios. It simplifies access management, ensures only authorized users reach critical resources, and supports compliance with security policies.