Jan 11, 2026
Managing access across multiple cloud platforms is complicated. Each provider - AWS, Azure, Google Cloud - has unique rules for permissions, roles, and identity management, making Role-Based Access Control (RBAC) harder to implement. This complexity increases the risk of security breaches, misconfigurations, and operational errors.
To simplify multi-cloud RBAC:
These strategies reduce complexity, improve security, and help organizations manage access across clouds more effectively.
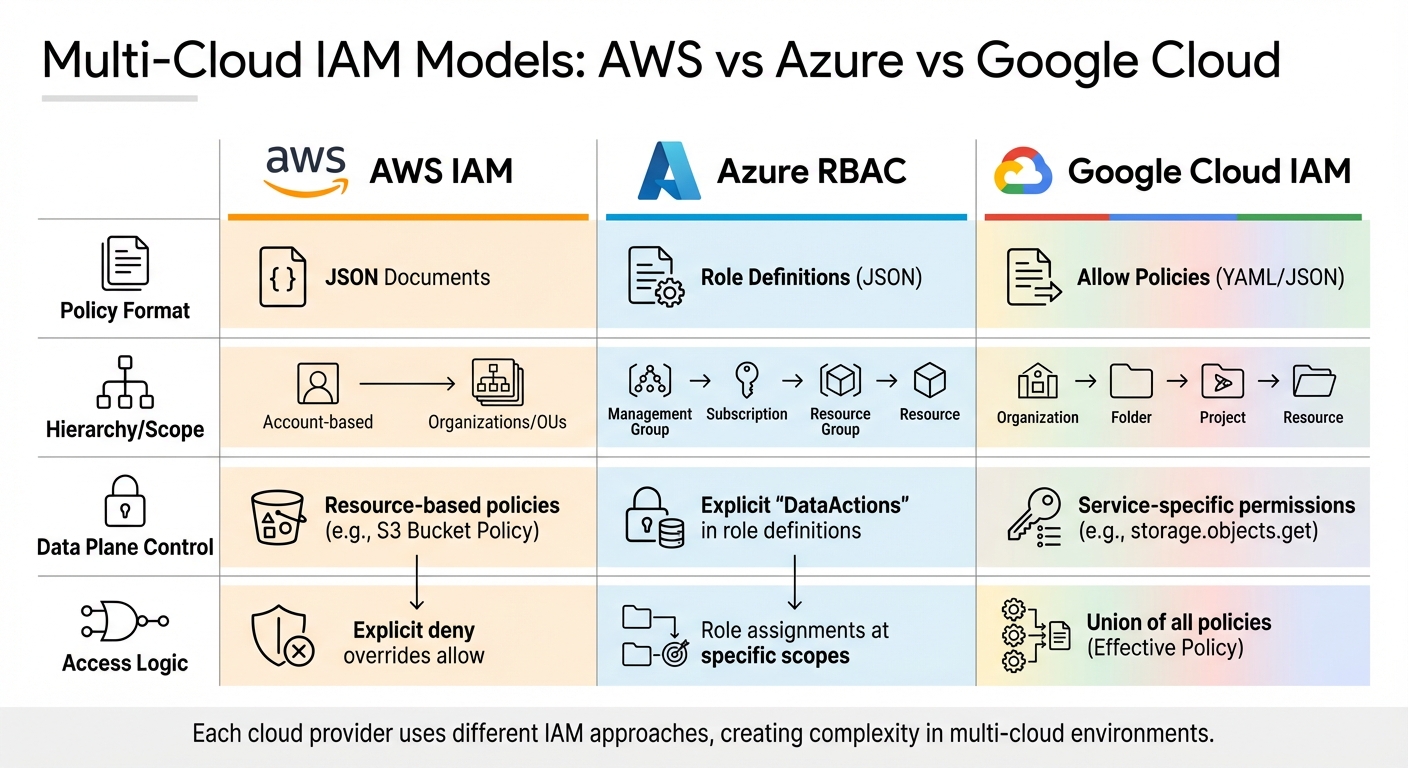
AWS vs Azure vs Google Cloud IAM and RBAC Comparison
Each major cloud provider approaches Identity and Access Management (IAM) differently, creating a patchwork of systems that organizations must navigate. For example, AWS uses JSON-based policies, separating identity-based policies from resource-based ones. Google Cloud organizes its permissions through a strict hierarchy - Organization > Folder > Project > Resource - where permissions cascade downwards through allow policies that link a principal to a role on a particular resource. Azure, on the other hand, relies on role assignments defined by three components: a security principal, a role definition, and a scope (such as Management Group, Subscription, Resource Group, or Resource).
But the differences don’t stop at structure. AWS employs an explicit deny system, where any deny statement takes precedence over allows. Google Cloud combines inherited policies into an effective policy using a union approach, while Azure separates management plane operations ("Actions") from data plane operations ("DataActions") in its role definitions. These variations force security teams to juggle multiple systems, increasing both operational complexity and the likelihood of misconfiguration. This fragmented landscape not only adds overhead but also complicates efforts to establish unified authorization across platforms.
| Feature | AWS IAM | Azure RBAC | Google Cloud IAM |
|---|---|---|---|
| Policy Format | JSON Documents | Role Definitions (JSON) | Allow Policies (YAML/JSON) |
| Hierarchy/Scope | Flat (Account-based) with Organizations/OUs | Management Group > Subscription > Resource Group > Resource | Organization > Folder > Project > Resource |
| Data Plane Control | Resource-based policies (e.g., S3 Bucket Policy) | Explicit "DataActions" in role definitions | Service-specific permissions (e.g., storage.objects.get) |
| Access Logic | Explicit deny overrides allow | Role assignments at specific scopes | Union of all policies (Effective Policy) |
These distinctions have a direct impact on API authorization, as the next section explores.
The fragmented nature of IAM models creates significant challenges for unified API authorization. Each cloud platform uses its own credential formats and logic. For example, AWS employs Signature Version 4 (SigV4) for API requests, while Azure and Google Cloud rely primarily on OAuth 2.0 and service principals.
A real-world example from February 2024 highlights this issue: a developer working with Azure RBAC faced "403 Authorization failed" errors due to the complex misconfiguration of role assignments for multiple system-assigned managed identities. Even with adherence to best practices, inconsistencies in authorization methods across platforms can lead to operational disruptions.
To address these challenges, organizations can implement a centralized Identity Provider (IdP) like Okta, Azure AD, or Google Workspace. This approach allows users to authenticate once with the IdP and receive temporary security credentials to assume roles in their target cloud environments. By eliminating the need for long-term passwords or access keys, this method reduces security risks.
For applications operating across multiple clouds or on-premise, workload identity federation provides a way to exchange local identity tokens for temporary cloud credentials. This minimizes the reliance on hardcoded secrets, further enhancing security.
Another key strategy is decoupling authorization logic from application code by using a centralized Policy Decision Point (PDP). This setup prevents accidental changes by developers and simplifies auditing processes. Declarative languages like Cedar or Rego (used in Open Policy Agent) enable consistent, machine-readable authorization logic that works across different programming languages and cloud providers. By translating unified RBAC policies into the formats each cloud platform requires, this abstraction layer eliminates the need for security teams to manually manage separate policy sets for AWS, Azure, and Google Cloud.
The rise of multi-cloud environments and microservice architectures has created fertile ground for an explosion of roles. With each cloud provider using its own terminology, permissions can quickly spiral out of control, leaving teams to juggle an overwhelming number of access configurations.
Often, organizations create job- or task-specific roles without fully considering their long-term implications. This practice introduces operational risks. As highlighted in the AWS Cloud Adoption Framework: "Role and policy sprawl can quickly become technical debt that can weaken your security posture and complicate audit and compliance matters". Over-provisioned roles amplify the potential damage of compromised accounts, increasing the "blast radius" and opening doors for privilege escalation - such as attackers inheriting permissions from deleted users. On top of this, managing permissions across multiple cloud systems often leads to human errors, which remain a major contributor to cloud security breaches.
Frequent changes in personnel, systems, and cloud features further erode carefully crafted least-privilege settings. As the AWS Security Blog aptly notes: "Perfect least privilege can cause maximum effort". Trying to maintain precise least-privilege policies manually often creates friction between security teams and developers who need flexibility and speed.
To tackle role sprawl, organizations can move from traditional Role-Based Access Control (RBAC) to Attribute-Based Access Control (ABAC). ABAC uses tags on resources and users to manage permissions dynamically, reducing the need for countless individual roles. For instance, a consistent tagging strategy like access-project = Heart across all resources allows for automated scaling and authorization adjustments without requiring manual policy updates. This approach significantly reduces the number of policies compared to managing hundreds of static roles.
Automation tools like AWS IAM Access Analyzer and CIEM can help enforce least-privilege principles by starting with broad permissions and refining them based on actual usage data. Additionally, permission boundaries can restrict access rights, ensuring that even if developers create new roles, they can't escalate their privileges beyond predefined limits. Adopting a zero-trust model - where no permissions are granted by default and only essential access is provided - further strengthens security.
These strategies not only help control role sprawl but also lay the groundwork for improved visibility across multi-cloud environments. By integrating automation with centralized monitoring, organizations can better manage permissions and enhance their overall security posture.
Automation is a key enabler of unified oversight across cloud platforms. A centralized Identity Provider (IdP) and Policy Decision Point (PDP) simplify credential management and ensure consistent enforcement of security policies.
When paired with CIEM tools that analyze usage data across different environments, security teams gain the insights they need to detect permission sprawl early. This proactive approach helps mitigate risks before they evolve into larger security threats.
Managing Role-Based Access Control (RBAC) across multiple API gateways can quickly spiral into chaos. Each provider - whether it's AWS API Gateway, Azure API Management, or Google Cloud Endpoints - has its own unique approach to authentication and authorization. This forces teams to juggle separate configurations, certificates, and API keys for every platform. Add service meshes like Istio to the mix, and the problem compounds. In Kubernetes environments, for example, identity-based policies and mutual TLS (mTLS) often operate at the service level rather than the gateway layer, further complicating things.
This lack of uniformity creates more than just headaches - it opens up security gaps. Consider this: only 27% of organizations maintain a complete inventory of their APIs, meaning most companies don’t even know where sensitive data might be exposed in their multi-cloud systems. That’s a serious issue when 84% of organizations report experiencing an API security incident within the past year. As Drew Firment, VP of Enterprise Strategy at Pluralsight, puts it:
"Each cloud provider approaches security differently in terms of security policies and shared responsibility models, and the onus falls on internal teams to identify and compensate for those differences".
Tackling this challenge requires a unified approach to securing API access across clouds. The key lies in creating a centralized control plane that can manage gateway clusters across all providers from a single interface. This doesn’t mean scrapping existing gateways; instead, it’s about establishing consistent configurations and policies that work across platforms. By standardizing on protocols like OAuth 2.0, OpenID Connect (OIDC), and JSON Web Tokens (JWT), identity federation can operate smoothly regardless of the cloud hosting your APIs.
Tools like Open Policy Agent (OPA) allow you to define RBAC rules as code, completely separating authorization logic from application code. For example, you can write declarative policies using Rego, which are then evaluated by a centralized Policy Decision Point (PDP). API gateways act as Policy Enforcement Points (PEPs), intercepting and validating requests against these central policies before they reach backend services. This setup ensures that authorization rules are applied uniformly across AWS, Azure, and Google Cloud.
To further enhance token security, a token exchange pattern can be implemented at the cloud edge. Here’s how it works: long-lived external tokens are swapped for short-lived, scoped internal tokens. This approach minimizes the risk of token replay attacks and protects against man-in-the-middle attacks in multi-cloud environments.

NanoGPT offers a real-world example of how centralized RBAC enforcement can streamline operations. This platform provides access to multiple AI models - such as ChatGPT, Deepseek, Gemini, Flux Pro, Dall-E, and Stable Diffusion - hosted across various cloud providers. To manage user permissions consistently, NanoGPT employs a single control point for RBAC.
By integrating a unified API gateway or OPA server, NanoGPT maps user roles to specific permissions for each AI model API, regardless of the underlying cloud provider. Given its pay-as-you-go model, precise tracking of API usage across all models is critical. Additionally, because user data remains local on devices, the authorization system only needs to validate tokens and enforce rate limits. This approach, which leverages JWT-based authentication and short-lived tokens, avoids storing sensitive information while maintaining security and efficiency.
This architecture enables NanoGPT to uphold consistent security policies while offering users seamless access to AI models across multiple clouds. It eliminates the need for users to manage separate credentials or deal with the complexity of the underlying infrastructure.
Managing cloud resources across AWS, Azure, and Google Cloud introduces some tricky challenges, especially when it comes to logging. Each platform uses its own logging system - AWS CloudWatch, Google Cloud Audit Logs, and Azure Monitor - which complicates event correlation and leaves gaps during audits. Misconfigurations are a major issue, often leading to breaches. These problems are made worse by inconsistent interpretations of standards like CIS, NIST, or PCI-DSS, as well as the unchecked growth of permissions caused by unused roles and orphaned service accounts. According to Cross4Cloud, centralizing operations is essential for gaining a unified view and optimizing cloud management, no matter where workloads are hosted.
To address these challenges, centralization is key. Start by aggregating all cloud-native logs into one system, such as BigQuery, Azure Log Analytics, or Microsoft Sentinel. Event-driven services, like OCI Events and OCI Functions, can stream audit data in near real-time, cutting down the delays that come with manual log collection.
Monitoring efforts should focus on critical areas: administrative actions (like policy updates or service account creation), data access (especially interactions with sensitive information), and policy-denied events (such as unauthorized access attempts). This approach helps maintain a least-privilege model on an ongoing basis. To further tighten security, automate access reviews with machine learning tools like IAM Recommenders or Access Analyzers. These tools can identify unused permissions and flag orphaned accounts. Additionally, implementing Just-in-Time (JIT) access - where elevated privileges are granted temporarily and only when needed - minimizes the attack surface while providing a clear audit trail of who accessed what and when.
When incidents occur, policy-denied logs are invaluable for identifying unauthorized access attempts quickly, allowing teams to isolate threats without delay. A centralized identity provider (IdP), such as Okta or Azure AD, enables you to revoke access across all cloud platforms instantly, ensuring rapid containment of potential breaches.
For emergencies, establish "break-glass" roles - temporary, high-privilege accounts designed for critical situations. These accounts should trigger detailed logging and be subject to thorough post-incident reviews. Assign these roles to service accounts rather than individual users, and allow temporary impersonation instead of permanent assignments. This setup provides a detailed audit trail and limits exposure to sensitive resources.
Finally, tools like Policy Analyzer can help verify access to critical resources and provide clear documentation for compliance audits. Together, these strategies create a robust multi-cloud RBAC governance framework, setting the stage for the next steps in implementation.
Poorly managed multi-cloud RBAC (Role-Based Access Control) can lead to serious security vulnerabilities. Each cloud provider has its own terminology and permission framework, resulting in fragmented IAM models that are tough to audit and prone to errors. Unchecked growth in permissions often leads to role explosion, which increases the risk of privilege creep and widens the impact of potential breaches. The challenges don’t stop there - integrating various API gateways and service meshes to enforce consistent policies can be a nightmare. Add to that the issue of fragmented logging, which slows down incident response times, and it’s clear why human error, driven by the complexity of managing these systems, is a leading cause of cloud-related security breaches.
To tackle these challenges, begin by centralizing identity management. Use a single Identity Provider (IdP), such as Okta or Azure AD, to enable SSO (Single Sign-On) across all cloud platforms and allow for instant access revocation when needed. Then, standardize roles and resource tagging to ensure policies are applied uniformly across AWS, GCP, and Azure environments. Adopt a zero-trust approach: start with no permissions and add only the minimum required access. Avoid using wildcards and implement granular, resource-specific policies to tighten security.
For machine identities, shift to Workload Identity Federation to replace long-lived API keys with temporary credentials issued through identity tokens. Incorporate Just-in-Time (JIT) access to grant permissions only when needed, ensuring they automatically expire after use. Finally, centralize logging and observability into a single pipeline or SIEM dashboard to avoid delays caused by switching between tools from different providers. Utilize Cloud Infrastructure Entitlement Management (CIEM) tools to automate permission analysis and fine-tune overly permissive roles based on actual usage data.
This structured approach lays the groundwork for seamless integration of tools like NanoGPT.
NanoGPT takes these principles and simplifies RBAC implementation through a unified platform. Acting as a centralized gateway for AI API access, it delivers the centralized control and consistent RBAC enforcement discussed throughout this article. With NanoGPT, you gain a single interface to manage role-based access, conduct security audits, and track compliance across tools like ChatGPT, Gemini, Deepseek, Flux Pro, Dall-E, and Stable Diffusion. Its pay-as-you-go pricing (starting at $0.10) eliminates subscription hassles, while local data storage ensures your sensitive information stays secure and private, meeting regulatory demands. NanoGPT streamlines control without the headache of navigating multiple cloud provider consoles.
A centralized Identity Provider (IdP) acts as the go-to system for managing user identities, groups, and permissions across various cloud platforms. Instead of juggling separate accounts for each service, you can handle everything - like creating, updating, or revoking access - from one central hub. When users log in, the IdP provides short-term tokens or credentials, enabling single sign-on (SSO) across platforms like AWS, Azure, and Google Cloud. This eliminates the hassle of remembering multiple passwords.
By integrating the IdP with HR or directory systems, any changes - such as onboarding new employees, updating roles, or handling terminations - are automatically synced across all connected clouds. This real-time update process reduces the risk of leaving unused or outdated credentials lingering around.
In multi-cloud environments, the IdP simplifies Role-Based Access Control (RBAC) by letting you define roles and permissions just once. These are then translated into equivalent permissions for each cloud provider, ensuring consistent access controls without duplicating effort. Plus, centralized audit logs offer a single, clear record of all user activity, streamlining compliance checks and making it easier to spot unusual behavior.
When each cloud provider’s identity and access management (IAM) system is handled separately, it can lead to a phenomenon known as role explosion. This happens when custom roles and permissions multiply rapidly, especially in multi-cloud setups. The result? Permission sprawl - a chaotic tangle of permissions that makes it tough to audit access, enforce consistent policies, and avoid misconfigurations. And misconfigurations, as you might guess, are one of the leading culprits behind cloud security breaches.
Another issue to watch for is privilege creep. Over time, users or service accounts can accumulate permissions they no longer need - often as new projects or services get added. This violates the principle of least privilege, leaving the door wide open for risks like unauthorized access, data leaks, or even privilege escalation attacks.
So, how do you stay ahead of these challenges? The key lies in centralizing identity management, sticking to least-privilege policies, and routinely reviewing and cleaning up outdated roles. These practices are essential for keeping your multi-cloud environment secure and manageable.
Automation simplifies enforcing the least-privilege principle by removing manual processes that often lead to over-permissioning or mistakes. With tools like Azure AD or Okta as central identity providers, automated systems can generate short-lived, role-based credentials instead of relying on permanent access keys. This approach ensures users only have the permissions they need for specific tasks - nothing more.
On top of that, automated tools like policy analyzers can evaluate real usage patterns and recommend minimal-permission policies. Infrastructure-as-code workflows and CI/CD pipelines can include automated checks to ensure least-privilege access is consistently enforced across platforms like AWS, Azure, and GCP. These methods help organizations maintain secure access control while keeping operations manageable and efficient.