Jan 4, 2026
The choice between TLS and DTLS can make or break the security and performance of your edge AI system. Here's the core takeaway:
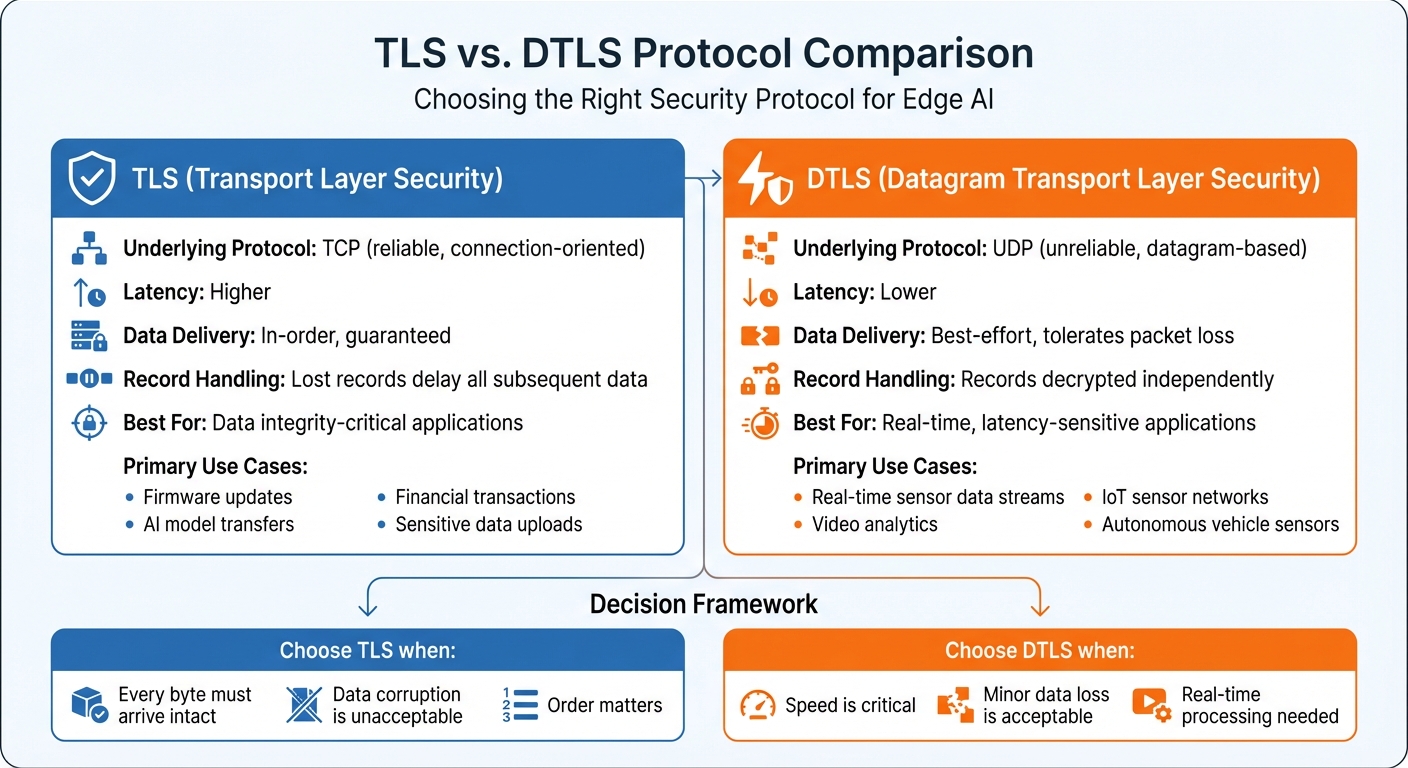
Quick Comparison:
| Feature | TLS (Transport Layer Security) | DTLS (Datagram Transport Layer Security) |
|---|---|---|
| Underlying Protocol | TCP (reliable, connection-based) | UDP (unreliable, datagram-based) |
| Latency | Higher | Lower |
| Data Delivery | In-order, guaranteed | Best-effort, tolerates packet loss |
| Use Cases | Firmware updates, AI models | Real-time data streams, IoT sensors |
Whether you prioritize reliability or speed depends on your edge AI deployment goals. Read on for a deeper dive into their features and trade-offs.
TLS vs DTLS Protocol Comparison for Edge AI Security
TLS establishes a secure, connection-oriented channel over TCP by utilizing two main components: the Record Protocol, which handles data encapsulation, and the Handshake Protocol, which manages authentication and key negotiation. This layered design makes it relatively simple to secure an application - TLS essentially acts as a bridge between the application and TCP layers.
It supports various authentication methods, such as Pre-Shared Keys (PSK) for devices with limited memory, Raw Public Keys, and the more traditional X.509 Certificates.
TLS 1.3 represents a significant leap forward compared to earlier versions. It reduces handshake latency, often completing the process in just a single round-trip. In some cases, it even supports 0-RTT resumption, allowing secure reconnections without the need for a full handshake. Additionally, TLS 1.3 removes outdated cryptographic techniques that previously posed security risks.
These features make TLS a powerful tool for ensuring secure communications, particularly in scenarios like edge applications where reliability and security are paramount.
TLS brings several benefits, especially for edge AI environments where maintaining data integrity and secure reconnections is crucial.
One of its standout benefits is its maturity and widespread adoption. TLS is the backbone of secure communications for web browsing, email, and cloud APIs, making it easy to integrate into existing systems.
Another important advantage is forward secrecy, particularly in TLS 1.3. This ensures that even if a long-term private key is compromised, past communication sessions remain secure. This feature is especially valuable for edge devices that often face resource constraints.
TLS also supports session resumption, which reduces the need for full handshakes during frequent reconnections. This is a significant advantage in edge environments where devices may reconnect often. For TLS 1.2, extensions like renegotiation_info and extended_master_secret can help address known vulnerabilities.
Despite its strengths, TLS does have limitations, particularly in resource-constrained edge deployments.
One of the key challenges is that TLS operates over TCP, which means it cannot secure unreliable datagram traffic. As Eric Rescorla, CTO of Firefox at Mozilla, explains:
"The primary advantage of TLS is that it provides a transparent connection-oriented channel... However, TLS must run over a reliable transport channel -- typically TCP. Therefore, it cannot be used to secure unreliable datagram traffic."
This reliance on TCP introduces head-of-line blocking. If a single TLS record is lost, all subsequent records are held up until TCP retransmits the missing data. For edge devices with limited resources, this can create significant delays.
Additionally, the TLS handshake process requires strict message ordering. In environments with high latency or frequent packet loss, establishing a secure connection can become sluggish. The certificate chains exchanged during the handshake often consume a large portion of bandwidth, which can be problematic for networks with limited capacity.
Even with the performance improvements in TLS 1.3, the protocol still assumes a certain level of computational power, which may be too demanding for devices with severe resource constraints.
DTLS takes the core principles of TLS and adapts them for use over UDP, a protocol known for its unreliability. It ensures that datagram semantics are preserved, even when packets arrive out of order or are lost along the way.
"The basic design philosophy of DTLS is to construct 'TLS over datagram transport'."
One standout feature of DTLS is the inclusion of sequence numbers in every record. This allows receivers to decrypt packets independently, meaning if one packet is lost, the others can still be processed without issue. This is a major improvement over TLS, where the loss of a single record can disrupt the decryption of subsequent ones.
To handle UDP's natural unreliability during connection setup, DTLS uses retransmission timers and message sequence numbers in its handshake process. It also employs a stateless cookie exchange to safeguard against denial-of-service (DoS) amplification attacks, a critical defense for devices operating at the edge of the internet.
DTLS 1.3, introduced in April 2022, brought in Connection IDs (CIDs). These enable secure communication sessions to persist even when a device's IP address or port changes. This is especially handy for mobile devices that switch between Wi-Fi and cellular networks.
These features make DTLS particularly well-suited for latency-sensitive environments, like edge computing.
DTLS has a clear edge over TLS when it comes to minimizing latency. By avoiding the overhead associated with TCP, DTLS is ideal for scenarios where speed takes priority over absolute reliability. It ensures real-time communication, even in cases where some packets are lost, making it a great fit for applications like live video streaming or continuous sensor data feeds.
Another strength lies in its ability to handle packet loss and reordering gracefully. As RFC 9147 explains:
"The behavior of such applications is unchanged when the DTLS protocol is used to secure communication, since the DTLS protocol does not compensate for lost or re-ordered data traffic."
DTLS 1.3 further improves efficiency by compressing record headers into a single format, which helps conserve bandwidth - a critical factor for constrained edge networks.
Despite its strengths, DTLS does come with some trade-offs. It doesn't guarantee delivery or in-order delivery of data, which can be problematic for applications that rely on every packet arriving intact. The handshake process can also be challenging, as messages may exceed the typical Path MTU (around 1,500 bytes), requiring fragmentation and reassembly. This can place additional strain on devices with limited resources.
Another issue lies in how some DTLS implementations handle errors. Records with invalid MACs are often discarded without terminating the connection, which can make error detection less transparent. As noted in RFC 6347:
"Because errors do not cause connection termination, DTLS stacks are more efficient error type oracles than TLS stacks."
While DTLS 1.3 introduces 0-RTT to reduce latency, this feature opens the door to potential replay attacks. Additionally, the DoS protection mechanism, which uses a cookie exchange during the handshake, adds an extra round trip. This can slightly impact performance in certain use cases.
When it comes to edge AI security, the choice between TLS and DTLS hinges on balancing guaranteed delivery with low latency. Here's a side-by-side look at their key differences:
| Feature | TLS (Transport Layer Security) | DTLS (Datagram Transport Layer Security) |
|---|---|---|
| Underlying Protocol | TCP (reliable, connection-oriented) | UDP (unreliable, datagram-based) |
| Latency | Higher due to TCP handshake and retransmission overhead | Lower; maintains datagram semantics for time-sensitive data |
| Reliability | Ensures ordered and guaranteed delivery | Best-effort; the application handles loss or reordering |
| Record Handling | Lost records delay all subsequent data | Records are decrypted independently, tolerating packet loss and reordering |
| DoS Protection | Standard TLS alerts | Stateless cookie exchange (HelloVerifyRequest) |
| Primary Use Cases | Web traffic (HTTPS), firmware updates, data-critical AI | IoT (CoAP), media streaming, real-time edge AI, gaming |
The way each protocol handles packet loss is a major differentiator. TLS, which operates over TCP, retransmits lost packets, potentially causing head-of-line blocking - where the loss of one packet delays all subsequent data. DTLS avoids this by using sequence numbers in each record, enabling independent decryption even when packets arrive out of order.
"Applications such as media streaming, Internet telephony, and online gaming use datagram transport for communication due to the delay-sensitive nature of transported data." (RFC 6347)
Another key distinction is DoS protection. DTLS employs a stateless cookie exchange mechanism to guard against IP spoofing and amplification attacks. TLS, on the other hand, relies on the stateful nature of TCP for its protective measures.
This comparison underscores the trade-offs between the two protocols. The following section will help you determine which option best suits your edge AI requirements.
When selecting between TLS and DTLS for edge AI, the decision boils down to three main considerations: latency sensitivity, data integrity requirements, and device resource limitations.
For resource-constrained devices, consider using PSK (Pre-Shared Keys) or Raw Public Keys as outlined in RFC 7925. Both TLS 1.3 and DTLS 1.3 support 0-RTT mode, which reduces latency during session resumption - an important feature for battery-powered devices that frequently wake up to transmit data.
If you opt for DTLS, keep in mind the Path Maximum Transmission Unit (PMTU) limitations, typically around 1,500 bytes. Records that exceed this size will need to be fragmented, which can be taxing for devices with limited resources. Additionally, DTLS does not support stream ciphers like RC4 because they require strict sequential processing, which conflicts with the nature of datagram-based transport.
Autonomous vehicles highlight the importance of DTLS in edge AI. For example, a self-driving car relies on sensor data from LiDAR, cameras, and radar to make split-second decisions. In these cases, processing sensor readings instantly is far more critical than waiting for TCP to resend lost packets.
"Applications such as media streaming, Internet telephony, and online gaming use datagram transport for communication due to the delay-sensitive nature of transported data." (RFC 4347)
Video analytics, like AI-driven facial recognition on security cameras, can tolerate the occasional loss of frames without compromising functionality. DTLS supports continuous streaming by preserving datagram semantics and preventing head-of-line blocking, which could otherwise cause stutters or delays in processing.
IoT sensor networks also benefit from DTLS's lightweight design, especially when paired with protocols like CoAP.
In latency-sensitive environments, DTLS shines by prioritizing speed and responsiveness. However, other critical applications may require the reliability of TLS.
While speed is crucial for some edge AI tasks, other scenarios demand absolute accuracy and data integrity.
TLS is indispensable for AI model updates and firmware downloads. When deploying a neural network model to an edge device, every byte must arrive exactly as intended. TLS ensures this by retransmitting lost packets and maintaining proper order.
Financial transactions and sensitive data uploads also rely on TLS for its robust reliability. Whether handling payment information or medical records, these systems cannot afford data loss or corruption. TLS provides the strict ordering and integrity checks needed for such high-stakes data exchanges. Although DTLS offers equally strong encryption, its method of discarding invalid records without terminating the connection makes it less suitable for tasks requiring flawless data transfer.
TLS further secures authentication and logging processes by ensuring that transmitted data is complete and properly ordered.
Choosing between TLS and DTLS boils down to your application's specific priorities. If ensuring data integrity is absolutely critical - like in firmware updates, financial transactions, or handling medical records - TLS is the better option. It guarantees that every byte of data arrives intact and in the correct order. On the other hand, DTLS shines in scenarios where reducing latency is more important than perfect data delivery. This makes it a great fit for real-time video analytics or IoT sensor networks, where occasional packet loss won't disrupt functionality.
Both protocols offer similar levels of security. In fact, many modern systems take a hybrid approach: they secure control traffic with TLS initially and then switch to DTLS for data transmission. This method strikes a balance between reliability and low latency.
"DTLS is used for delay sensitive applications (voice and video) as its UDP based while TLS is TCP based." - Meddane, Cisco Learning Network
For edge AI deployments, it's essential to consider the limitations of your devices. DTLS can be demanding for devices with limited resources, like those running on batteries or with low memory, due to the challenges of handling packet loss. In such cases, IoT-specific profiles like RFC 7925 can help by optimizing configurations for devices with restricted processing capabilities.
The protocol landscape is constantly evolving. New standards like QUIC are emerging to combine reliability with low latency, catering to the needs of edge AI. Always ensure you're working with the latest versions - TLS 1.3 and DTLS 1.3 address many vulnerabilities found in earlier versions and make secure deployment simpler. Ultimately, your choice should balance security and performance, especially in resource-constrained edge environments.
When deciding between TLS and DTLS, it all comes down to the communication needs of your edge AI application. TLS works best in situations where reliable and ordered data delivery is a must. For example, it’s perfect for transferring large AI model updates or sensitive information over TCP.
In contrast, DTLS shines in scenarios requiring low-latency communication over UDP, where some packet loss is acceptable. This makes it ideal for real-time data streams from sensors in devices with limited resources. Choosing the right protocol based on your application's demands ensures you strike the right balance between security and performance for your edge AI system.
DTLS provides TLS-level security, delivering encryption, authentication, and data integrity to safeguard against threats like eavesdropping, tampering, and message forgery. Unlike traditional TLS, DTLS is tailored for UDP datagrams, ensuring low latency while incorporating features such as replay protection and handshake mechanisms that can handle packet loss. These capabilities make DTLS an ideal choice for real-time, high-speed data streams commonly used in edge AI applications.
TLS can absolutely be tailored for edge devices with limited resources. By using lightweight IoT profiles and more efficient implementations, it's possible to reduce memory, bandwidth, and energy consumption. These adjustments allow even the most resource-constrained devices to maintain strong security for their communications.